Configure Networking
Contents
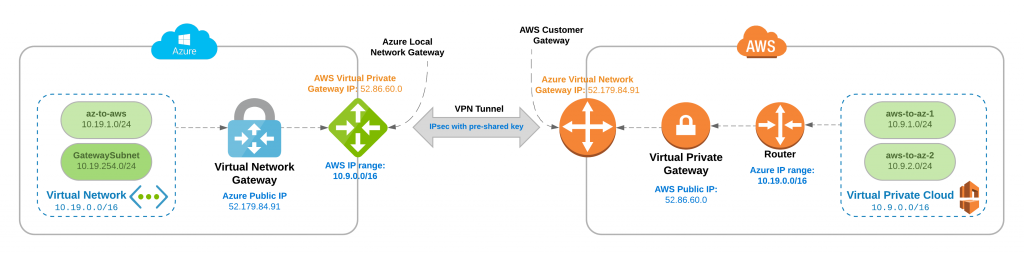
As of February, 2019, AWS supports IKEv2 which allows us to create a VPN between AWS and Azure without provisioning a Windows Server edge device in AWS. Thanks to this post for these instructions.
After completing the below steps, you will have the following networks and VPN tunnel configured (though with different public IPs):
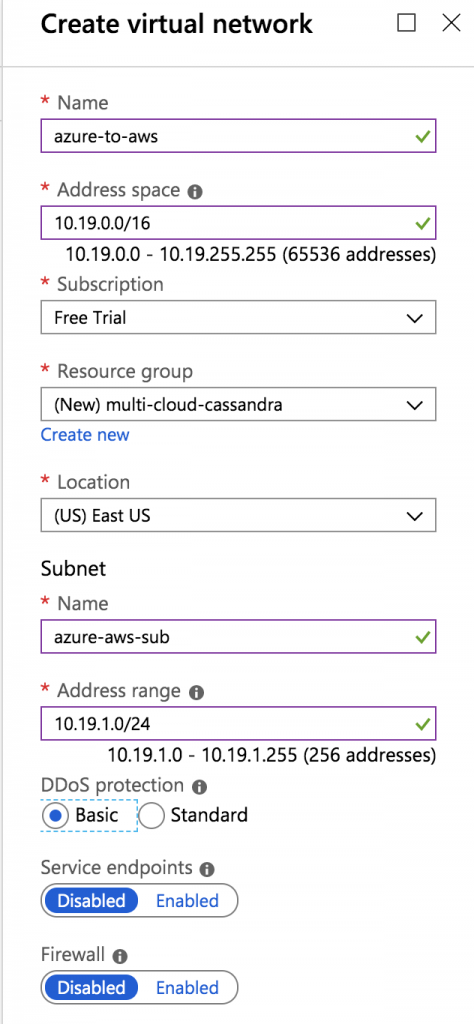
Create Azure Virtual Network
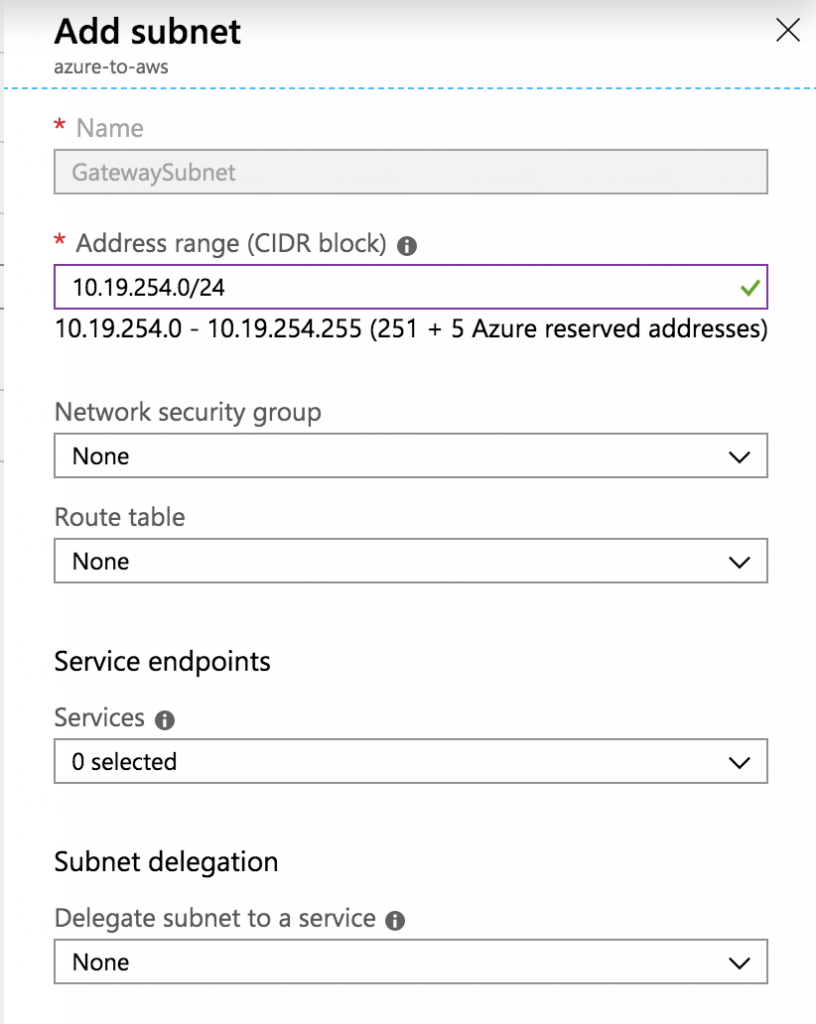
Add Gateway Subnet
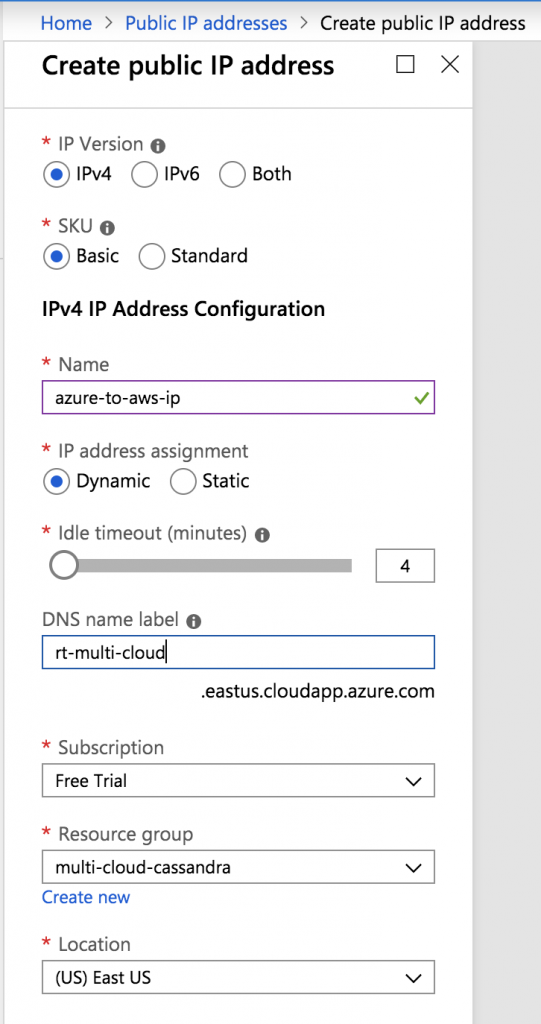
Create a Public IP
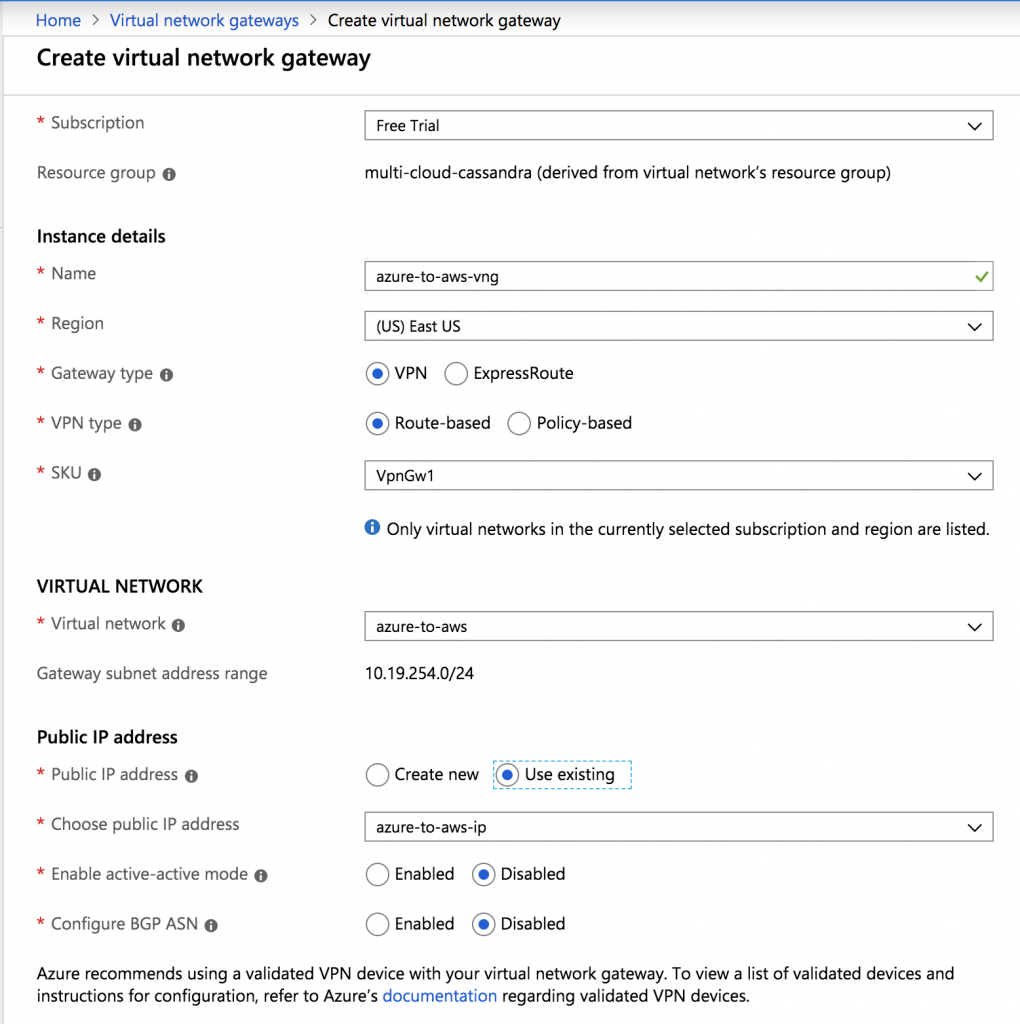
Create Virtual Network Gateway
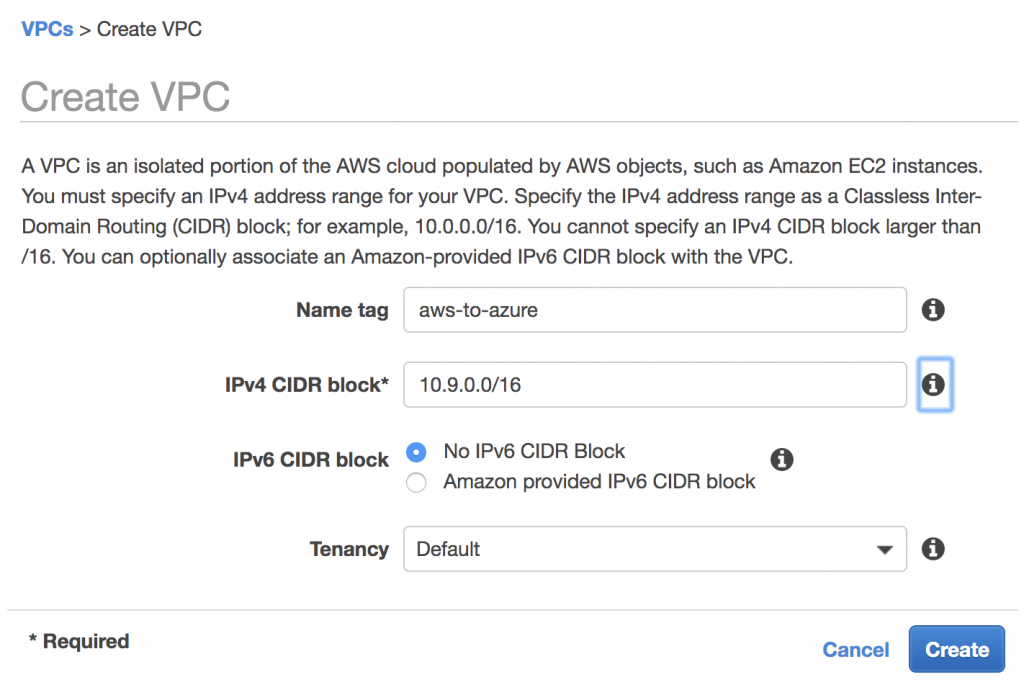
Create AWS VPC
Note the group ID of the default VPC security group that was created with the VPC. You will need this later on when creating the EKS cluster.
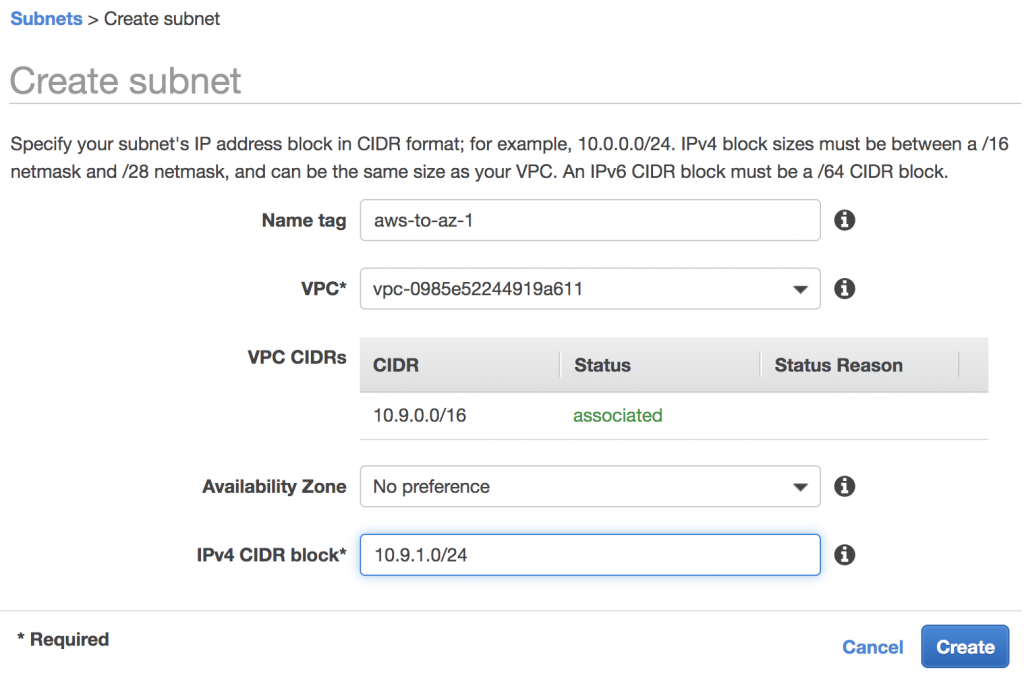
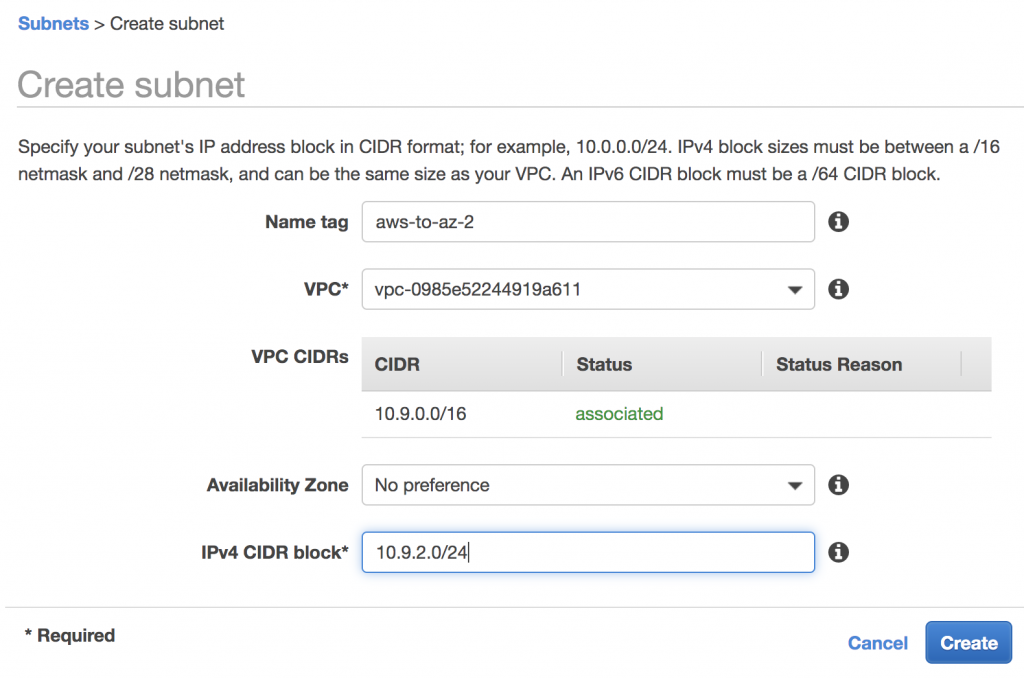
Create AWS Subnets
Amazon EKS requires at least 2 subnets in 2 different AZs, so we will create 2 subnets in the VPC.
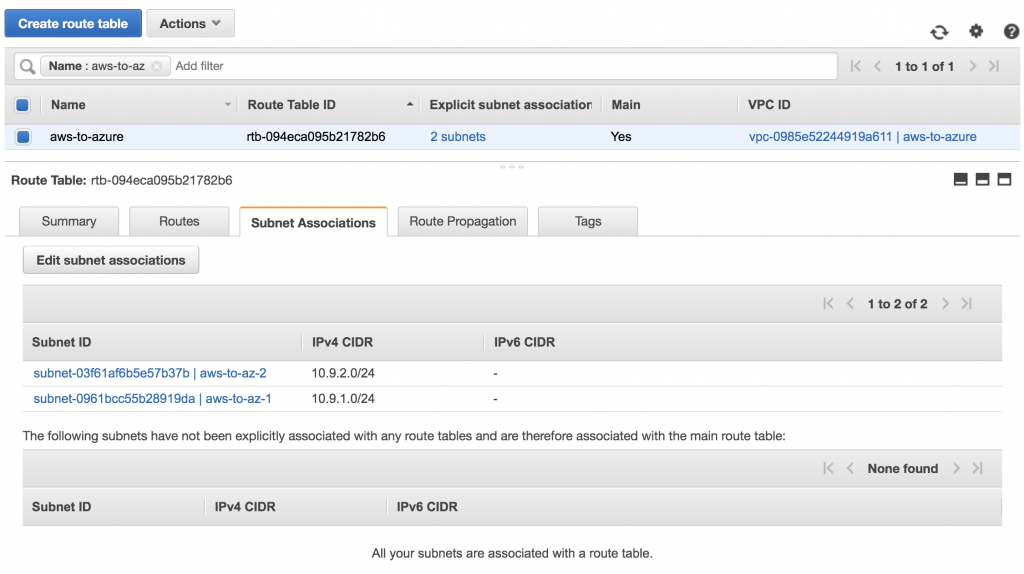
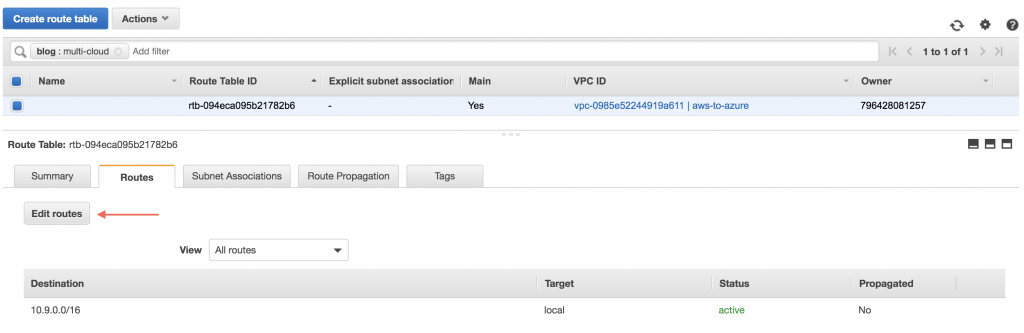
Also, edit the subnet associations of the VPC’s main route table and add both subnets. Your route table should look like this:
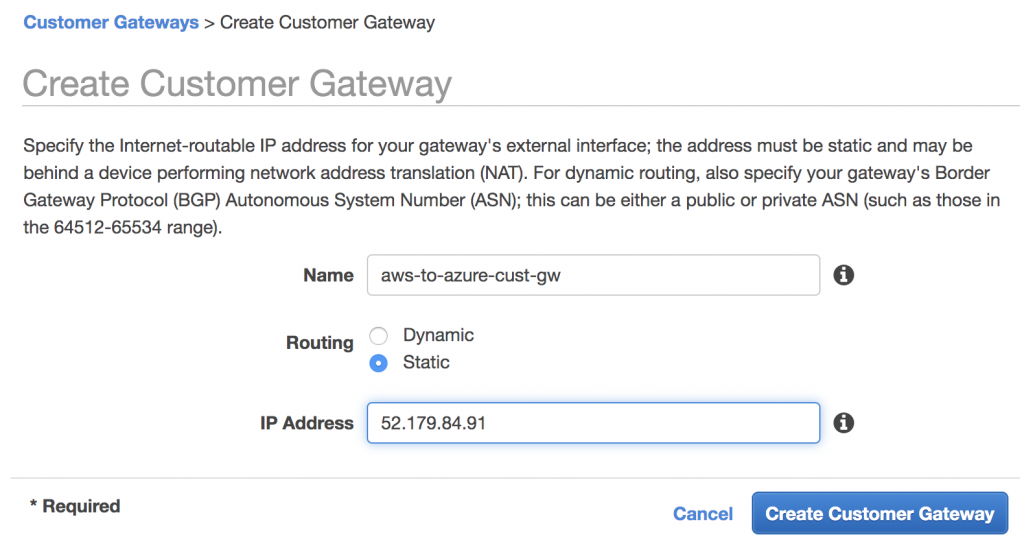
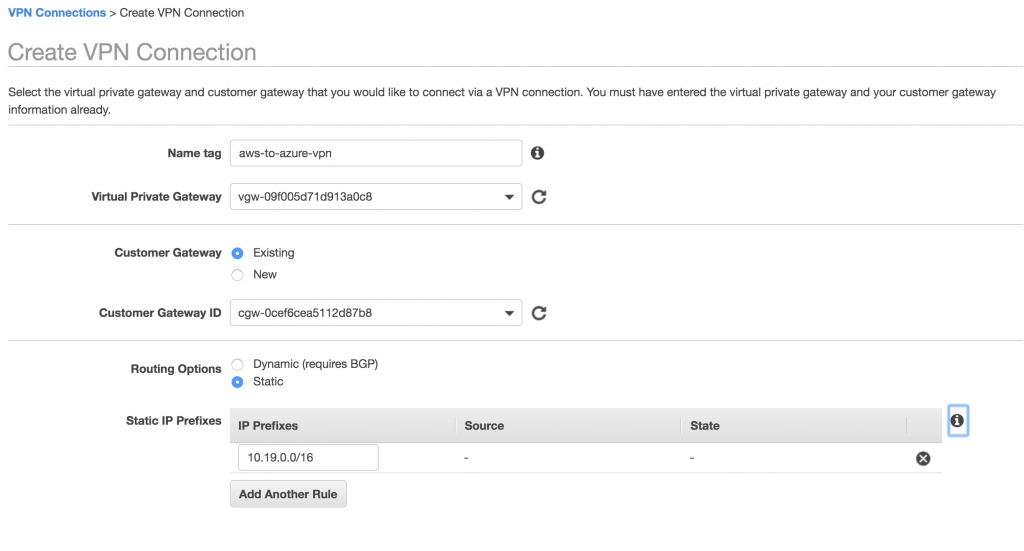
Create AWS Customer Gateway
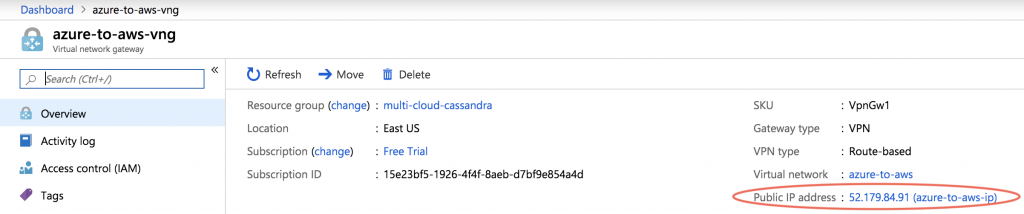
First get the public IP address of the Azure Virtual Network Gateway. This took about 30 minutes to appear in my Azure account.
Then create the AWS customer gateway from the VPN section of the VPC dashboard.
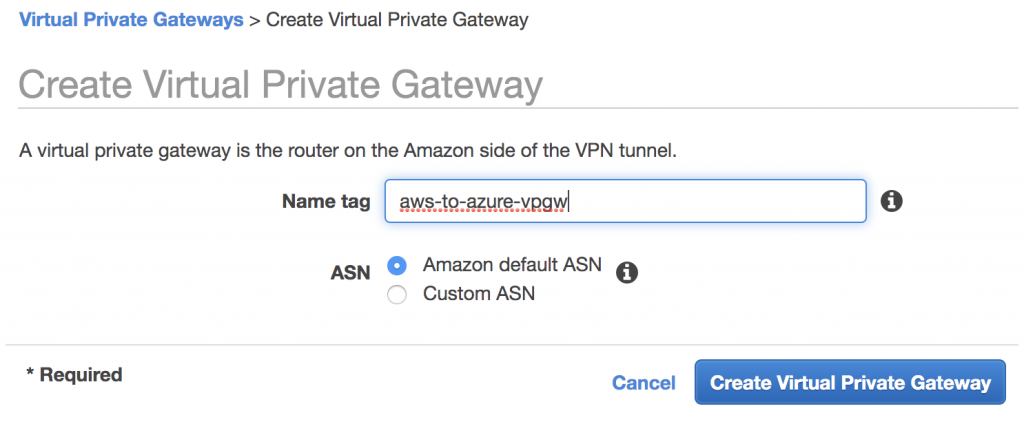
Create AWS Virtual Private Gateway
This is just below Customer Gateway in the VPC dashboard.
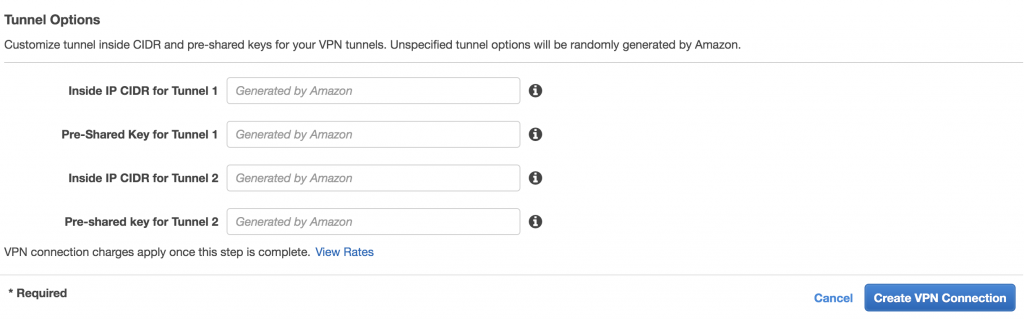
Create static site-to-site VPN connection
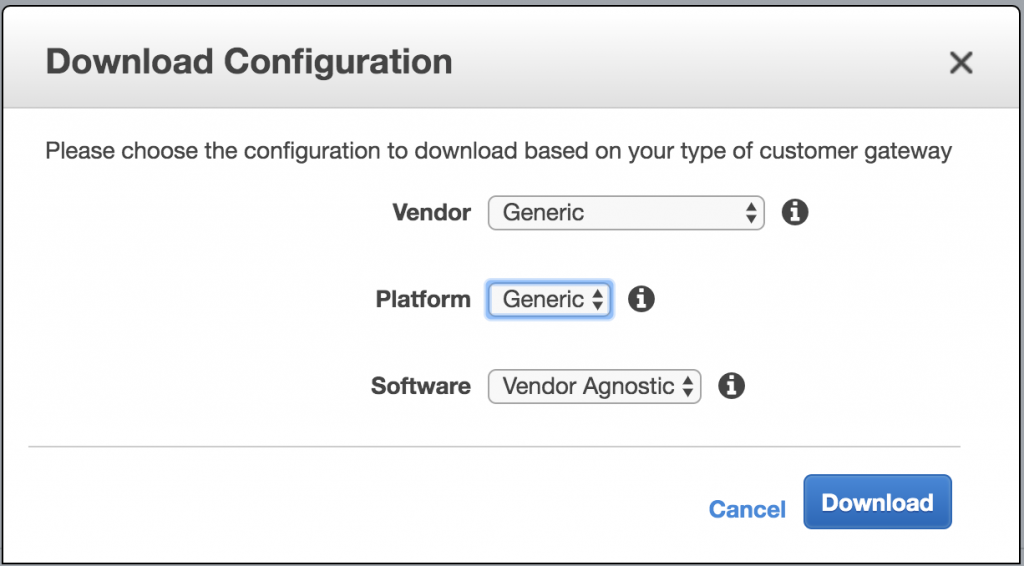
Download the generic VPN configuration file
You will need the following information from this file:
IPSec Tunnel #1 -> #1: Internet Key Exchange Configuration -> Pre-Shared Key
IPSec Tunnel #1 -> #3: Tunnel Interface Configuration -> Outside IP Addresses -> Virtual Private Gateway
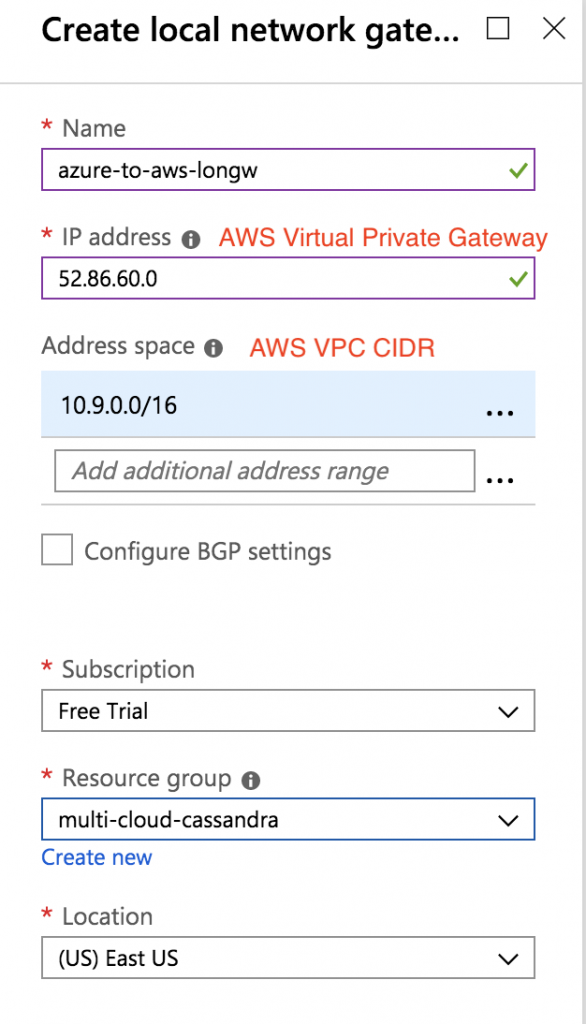
Create Azure Local Network Gateway
Configure this using the AWS Outside IP Addresses -> Virtual Private Gateway from above, and the AWS VPC CIDR.
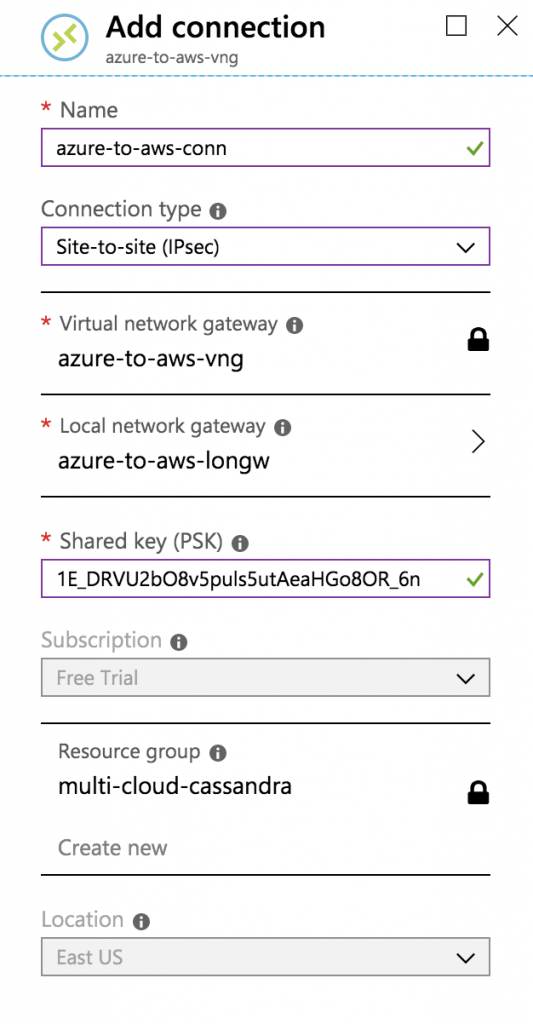
Create VPN Connection
From the Azure Virtual Network Gateway that you created earlier, click “Connections” and then “Add” to add a new connection.
Use the pre-shared key from the AWS VPN configuration file.
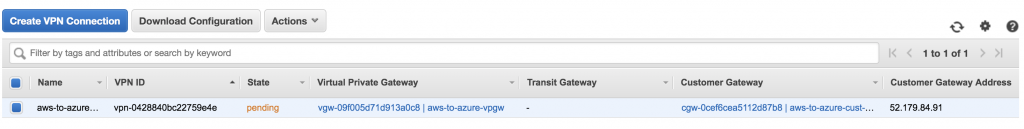
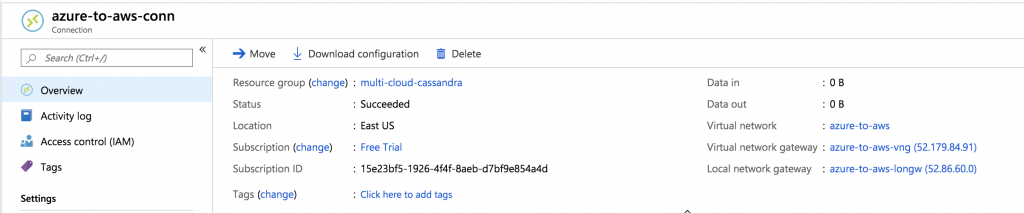
After several minutes, the connection should succeed.
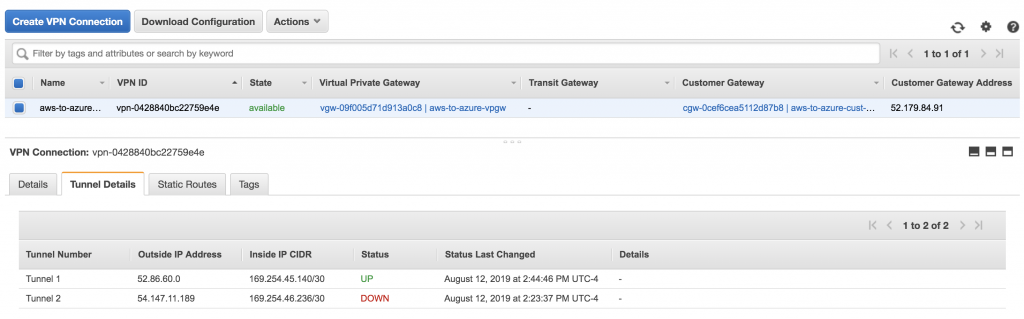
AWS should also show that tunnel 1 is up.
For this demonstration it was not necessary to create a 2nd tunnel.
Attach AWS Virtual Private Gateway to VPC
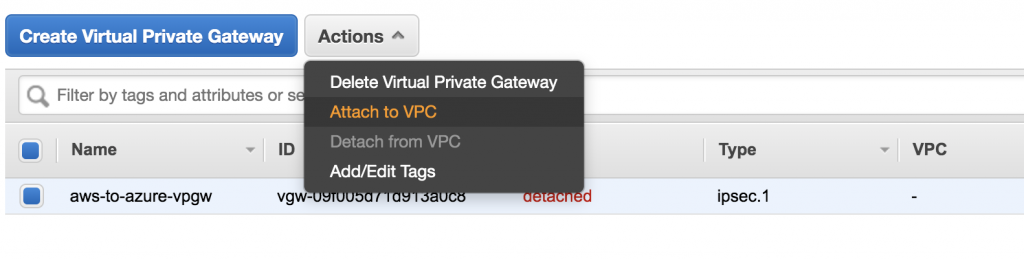
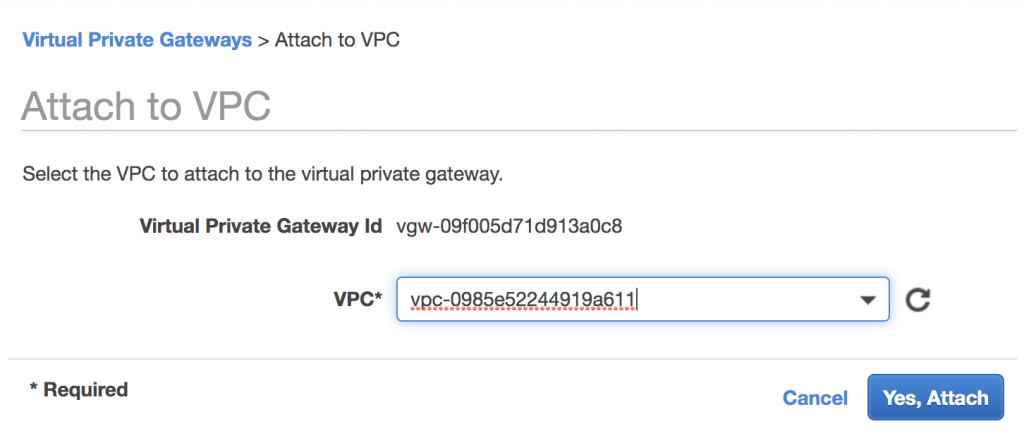
Add the Virtual Private Gateway to the AWS VPC Route Table
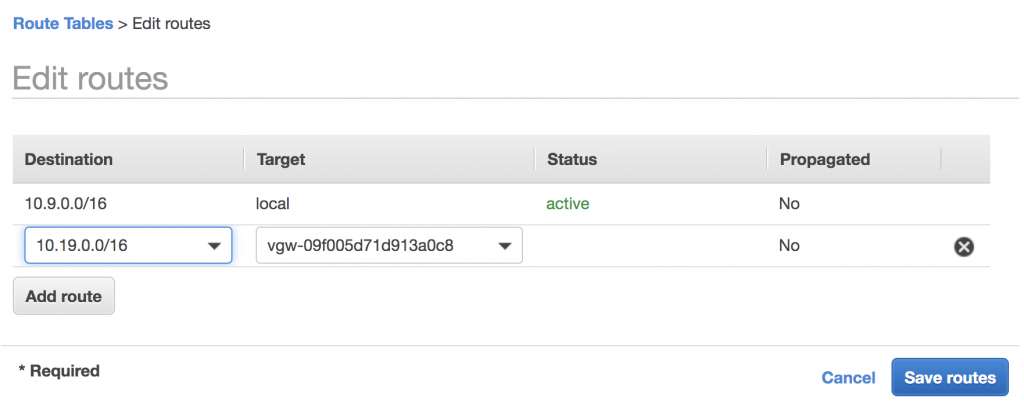
Test Connectivity
To test the connectivity between the Azure and AWS networks, first launch servers into the respective subnets. Then, modify the security group of the AWS server to allow all traffic from the Azure network (10.19.0.0/16).
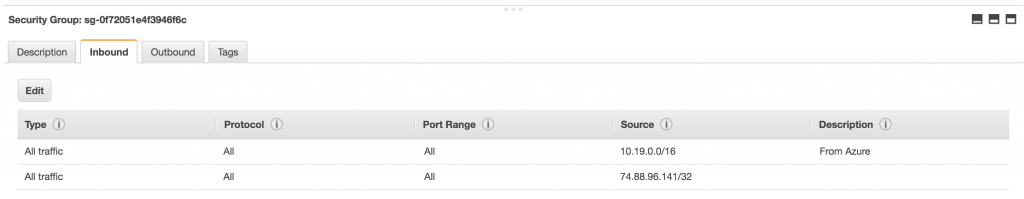
Additionally, in order to SSH to the AWS server from the Internet, you must add an internet gateway, attach it to the AWS VPC and add it to the route table.
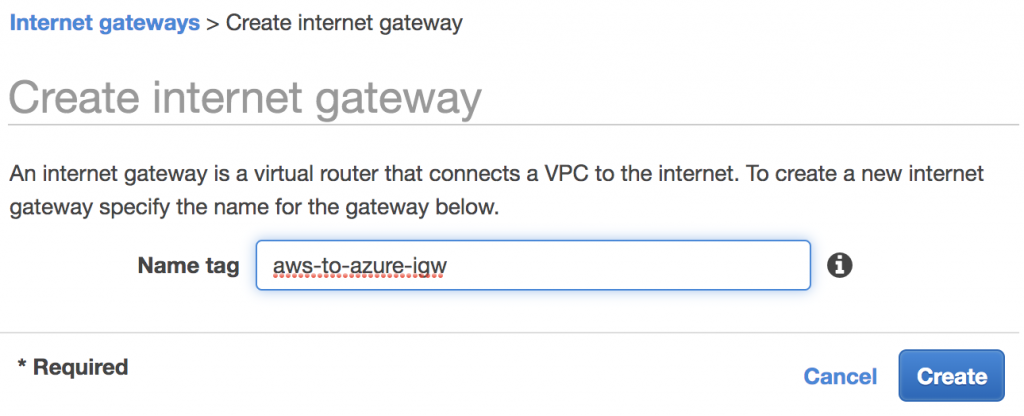
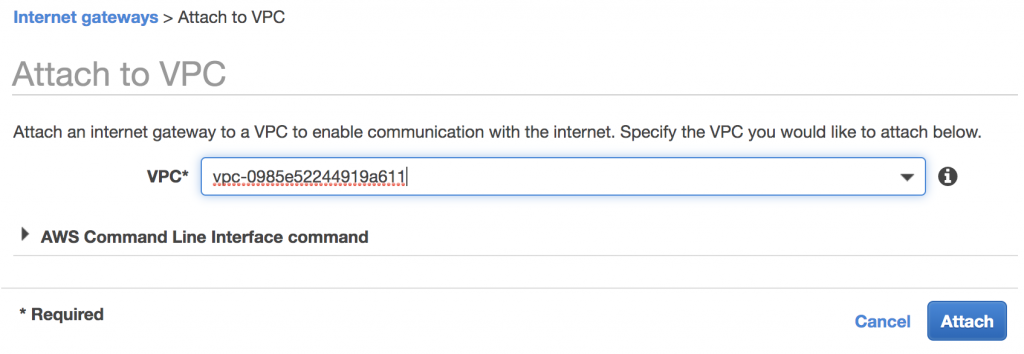
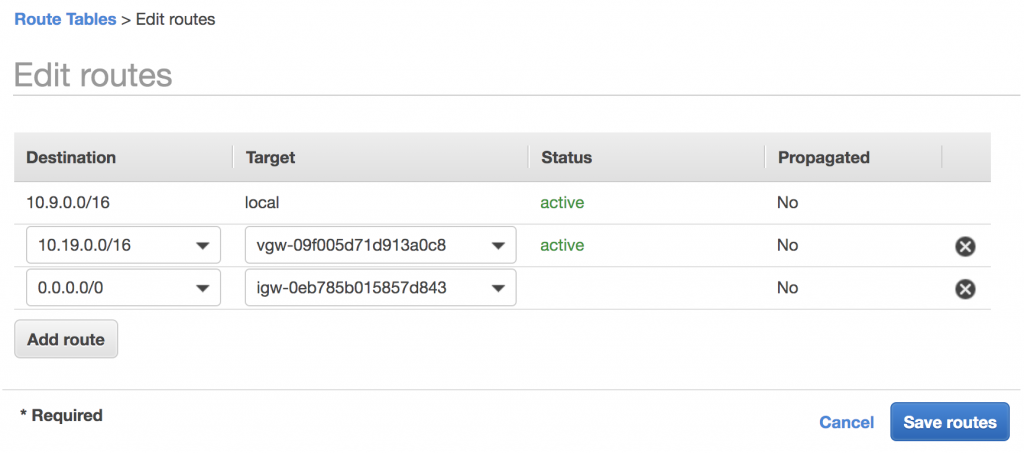
There were no additional configurations needed on the Azure side.
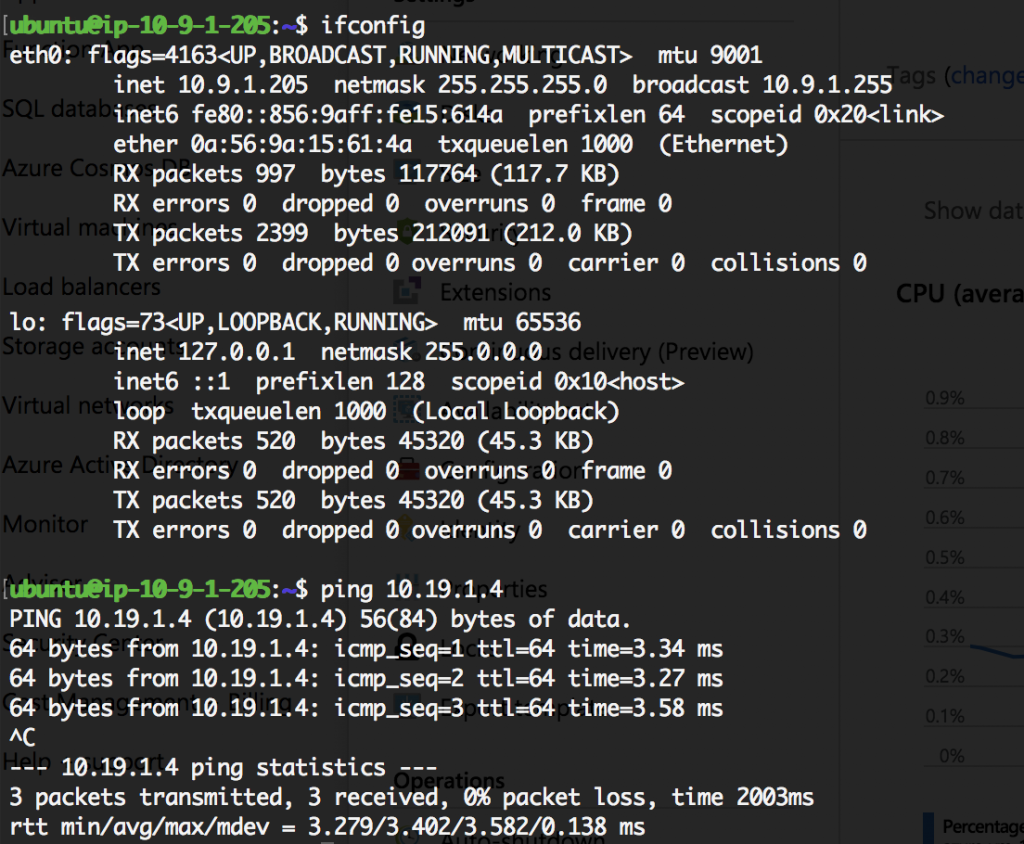
Connectivity was confirmed from AWS to Azure:
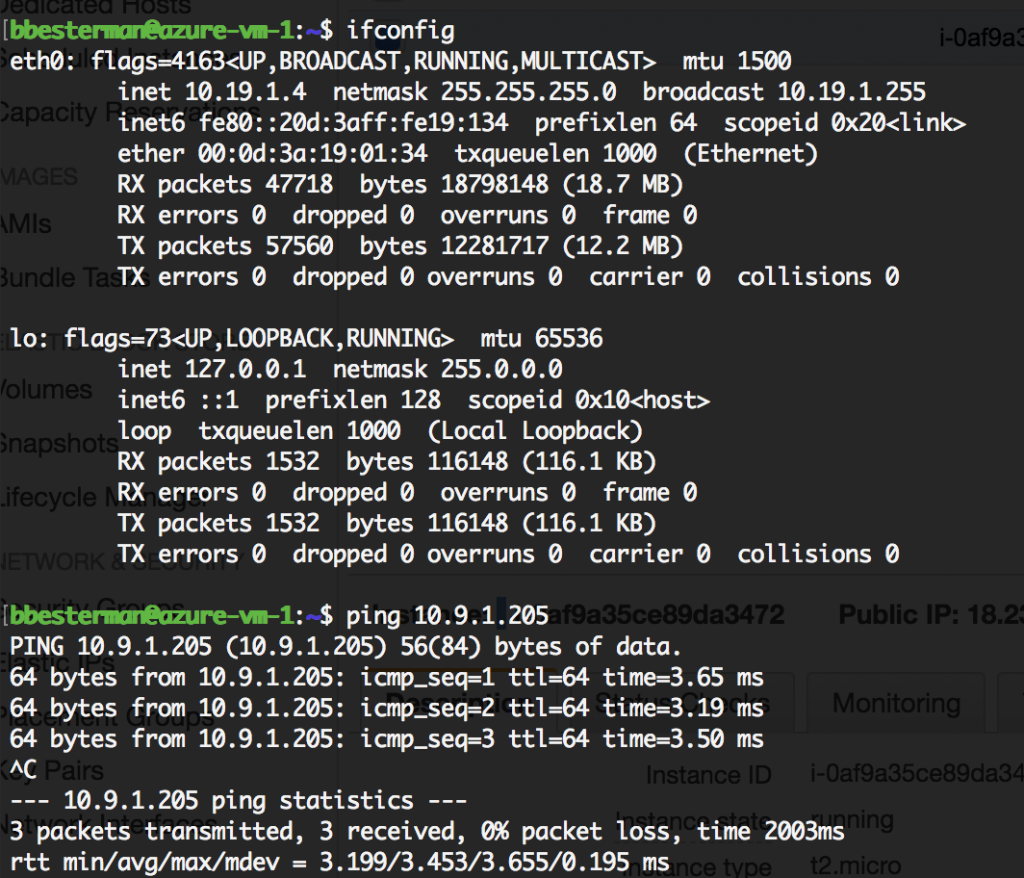
And from Azure to AWS:
With your networking completed, you are ready to install Kubernetes.